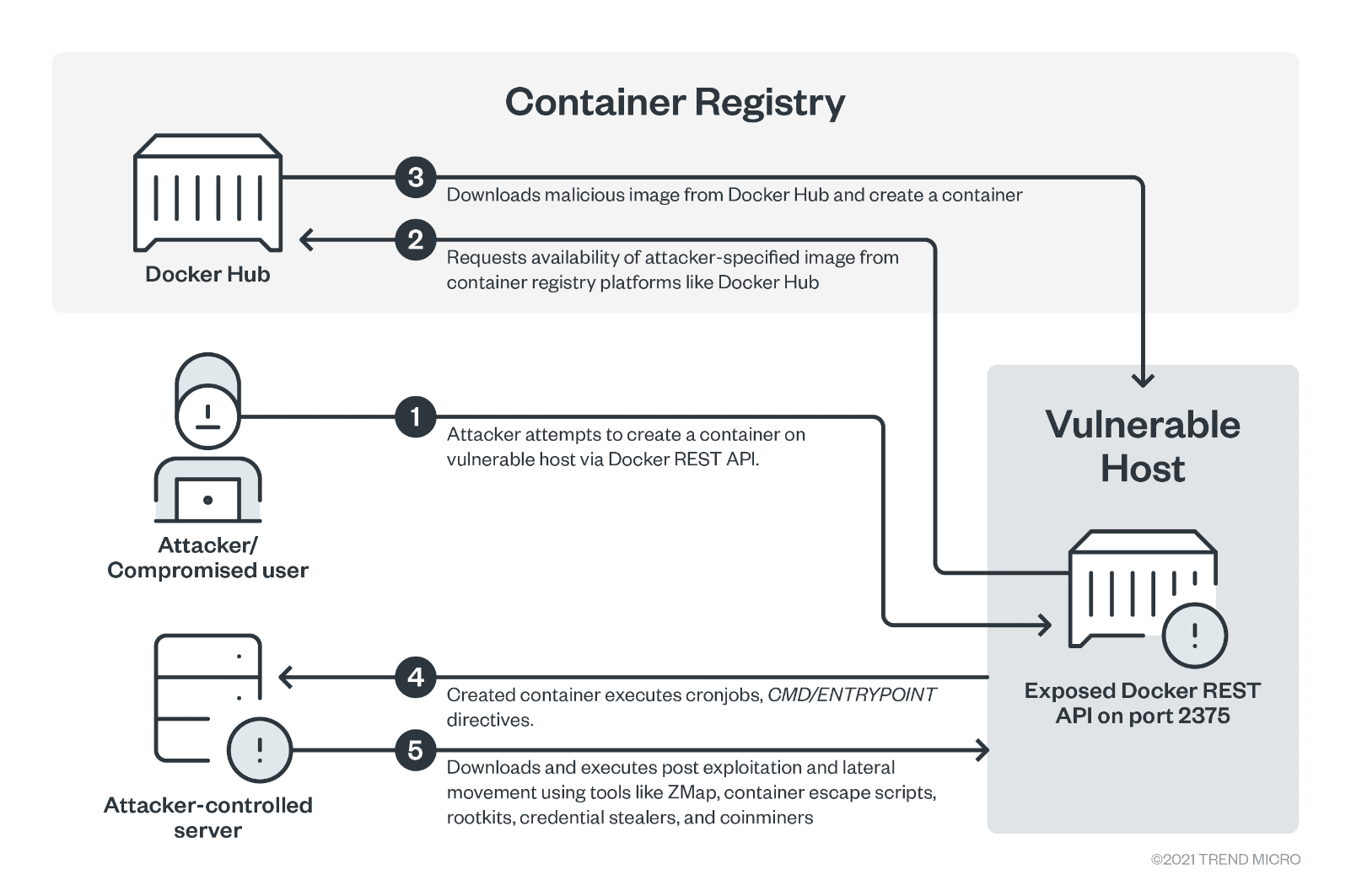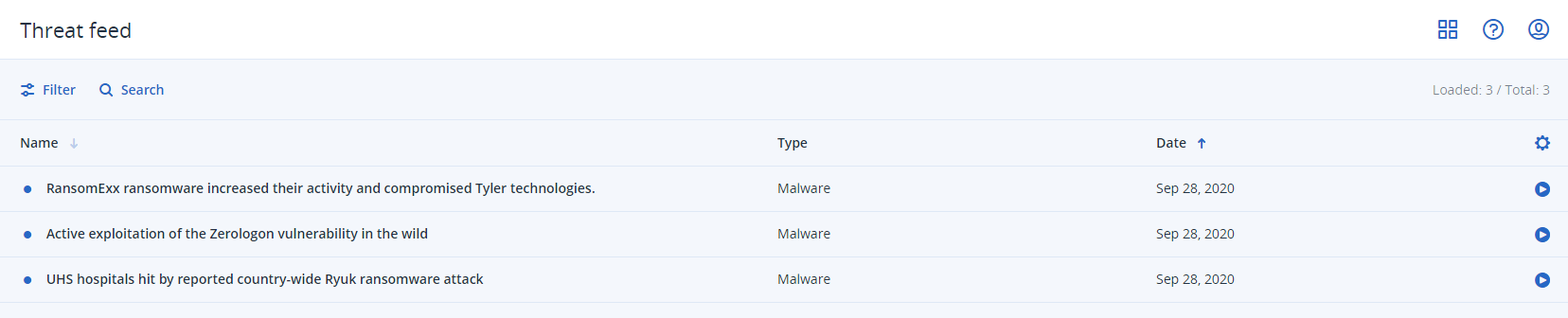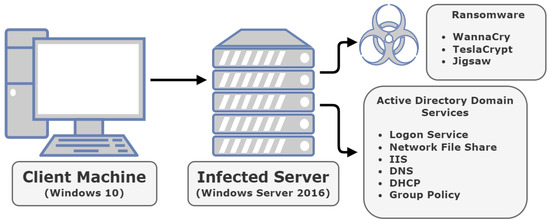
Sensors | Free Full-Text | Ransomware: Analysing the Impact on Windows Active Directory Domain Services | HTML
Solved] Complete Exercise 9.3, 'Using Avast! Antivirus,' from the Summary section of Ch. 9, 'Defending Against Virus Attacks,' of Network Defense an... | Course Hero


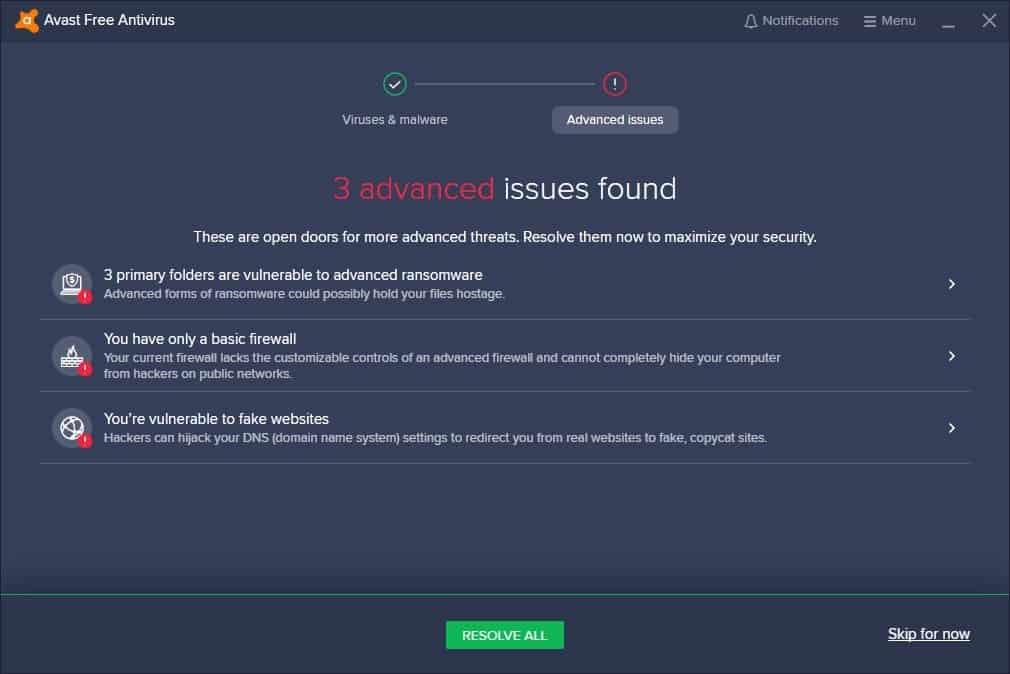







![Avast Antivirus Review 2022 [Updated] - Online Help Guide Avast Antivirus Review 2022 [Updated] - Online Help Guide](https://onlinehelpguide.com/wp-content/uploads/2020/03/Avast-Antivirus-Review-2020.jpg)